With every new system comes the challenge of adoption. We have all faced internal frustrations when introducing yet another solution that employees need to learn and use at work. The larger the company, the more people are involved. The more people are involved, the more confusion arises. To effectively manage change internally, we believe that everyone’s experience should be intuitive and seamless.
Visitor management solutions have three distinct users. The experience starts with the guest but also applies to the hosts (employees) and administrators (reception, operations, and security). A good software design principle is, not to overwhelm users with features that they don’t need – therefore making it easier to use and create a more controlled environment. To address this, we’ve created customizable user roles.
What are user roles?
User roles are a setting that determines the access level (or permissions) of a person who is authorized to use the browser-based portal. They give the account holder the ability to control what users can and cannot access or influence.
Why do they matter?
Managing who can make changes or access data can reduce issues and limit the level of technology adoption required of certain employees. For organizations with a large user base and a dynamic group of employees, it is critical to keep track of who has access to your system.
How should user roles be managed?
Within every organization, there will be active and passive users of a system. To start, define groups of individuals that are involved on distinct levels by job function, seniority and/or location. Once you are clear on their role, you need to decide on the features required to effectively use the system. As this can vary heavily across organizations and industries, make sure to choose a fully customizable software solution.
User roles for a visitor management system
To ensure organizations enjoy welcoming guests, we developed a user-friendly visitor management platform that is appropriate for each user. With our comprehensive Permission Bundle settings, you can customize who gets access to features and data.
Sign In Enterprise has two pre-defined user roles: Admin and Invite Only. Any employee who hosts visitors but does not influence the setup of the sign-in flow can be associated with the latter. This limits their access to pre-registering guests. Admins have more advanced user settings and can create additional, more distinct user roles for certain employees that require greater access to the system.
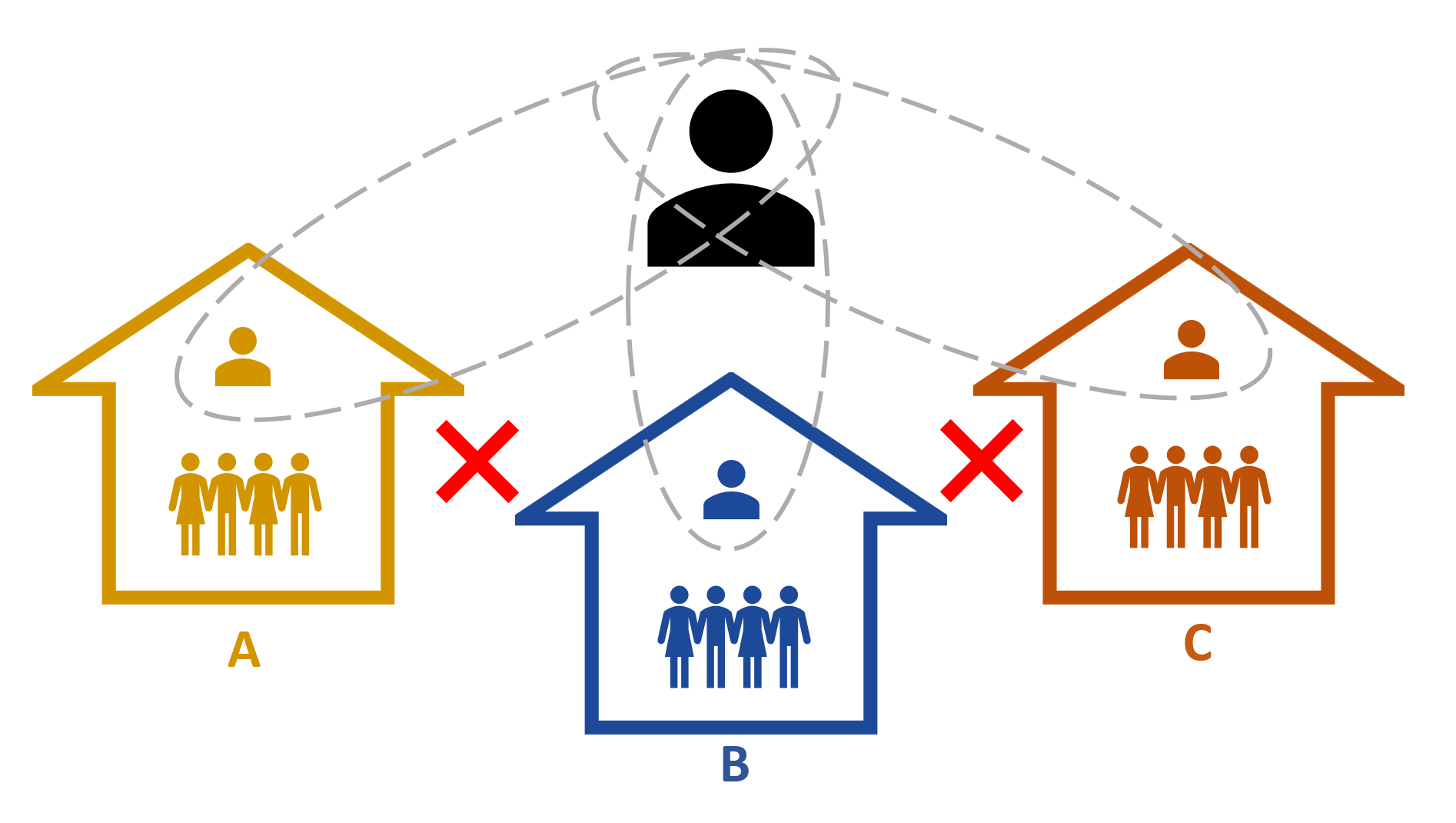
For instance, individuals in your marketing department could be given more access than general hosts, in order to control the branding of the visitor badges or the sign-in experience on the iPad. An admin might also be challenged with managing multiple sites and wants to limit access to location-specific visitor sign-in information for data security. To do so, they can create dedicated Permission Bundles for the receptionist at each location, whilst maintaining the full view himself. Each site can manage users independently.
With fully customizable user roles, each employee will only see what is relevant to them. Based on the access level the user will be able to see and access certain features when logging in. By streamlining the access levels, the platform remains easy to navigate while allowing for great flexibility.
For more detail on how to create Permission Bundles on Sign In Enterprise, watch this video or check out this article on the Sign In Enterprise Knowledge Base.

We are really excited about this new release! Get in touch with any questions, or book a personal demo if you are interested in finding out more.
